:: Historical
Since AirOS 4.2 there is an option available in Cisco’s WLAN controllers called Peer to Peer blocking. Previously a more lightweight version was presented to push all ARP request up-stream exiting the controller to the connected switch. This has been introduced as Peer-to-Peer Blocking with more enhancements onboard. So far for the history lessons.
Also Autonomous AP support this feature but is is know as Public Secure Packet Forwarding or PSFP for short.
:: Peer-to-Peer blocking
Mostly this can be a requirement for Guest oriented WLAN networks. As a company you want to provide Internet connectivity as a service to your customers. Security would be the responsibility of the user, hence you will provide the user with a disclaimer before they access the network allowing them to leave on time or use the service with their consent. Checked box for legal stuff = Done! Don’t blame us, we blame you.
The feature peer-to-peer blocking sounds perfect to provide this service without users mis-using the service (let’s run some captures and do some man-in-the-middle attacks to other guest users and see what data we can compromise and use). Also you don’t want users able to “see” each other via discovery services and accidentally expose data to other users. Although the security is the responsibility of the user, you can’t expect them to know how their OS works, how networks work and how to mitigate these potential issues.
For easy reading consider the following:
Centrally switched = Local Mode
Locally Switched = Flexconnect
Source: https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/8-8/FlexConnect_DG.html#pgfId-43785
:: How does it work?
We have three settings in this feature:
- disable: turn off this feature, allowing all communications;
- drop: drop traffic;
- forward up-stream: Let the upstream network figure it out.
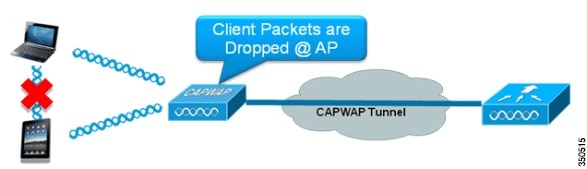
When enabling this feature (default set to disabled) the dot11 radio interface get instructed to protect communication between wireless clients (bridge-group group port-protected under the dot11 interface). For centrally switches this function lies with the controller itself because user and control traffic is centrally switched.
For locally switched AP’s they get a similar instruction on the dot11 interface. When communications from one client to another client is switched on the radio interface the protected-port kicks in. When the client communication leave the AP via the ethernet port to reach the other client, this feature is no longer respected and must rely on the underlaying network.
:: The scenario’s
On Local mode
Clients on the same AP and same Controller: Peer-to-peer blocking drop works;
Clients on different AP’s and same Controller: Peer-to-peer blocking drop works.
Flexconnect Mode
Clients on same AP and same controller: Peer-to-peer blocking drop works;
Clients on different AP’s and same controller: Peer-to-peer blocking drop doesn’t work;
Clients on different AP’s and different controller: Peer-to-peer blocking drop doesn’t work.
Note: Forward up-stream in Flexconnect mode will act as drop since we’re not tunneling user traffic back to the controller.
:: Unicast versus multicast
Peer-to-peer blocking can only handle unicast traffic. Multicast will not be dropped in any scenario.
:: What is needed for full end-to-end isolation?
My view on this: When traffic exits the “Wireless world” it depends on the underlaying network and features to be protected or not. In the above scenario’s we see that in flexconnect this only works in one scenario. The other scenario’s depicts that traffic is leaving the wireless network via the AP switch port and breaking out to the traditional network.
For this to work end-to-end you must design and install features like pVLAN’s or other microsegmentation features. For flexconnect you can implement Flexconnect ACL ingress to prevent these type of communications.
Designing and incorporating these features depends strongly on your type of network (small, medium, large, enterprise, etc), how many controllers you have, how many branch offices and how traffic can flow in your network locally and globally.
For small companies with just one location and one controller (or cluster) you can use this feature without any issues.
:: Resources
Some question not answered? The answer is 42!
