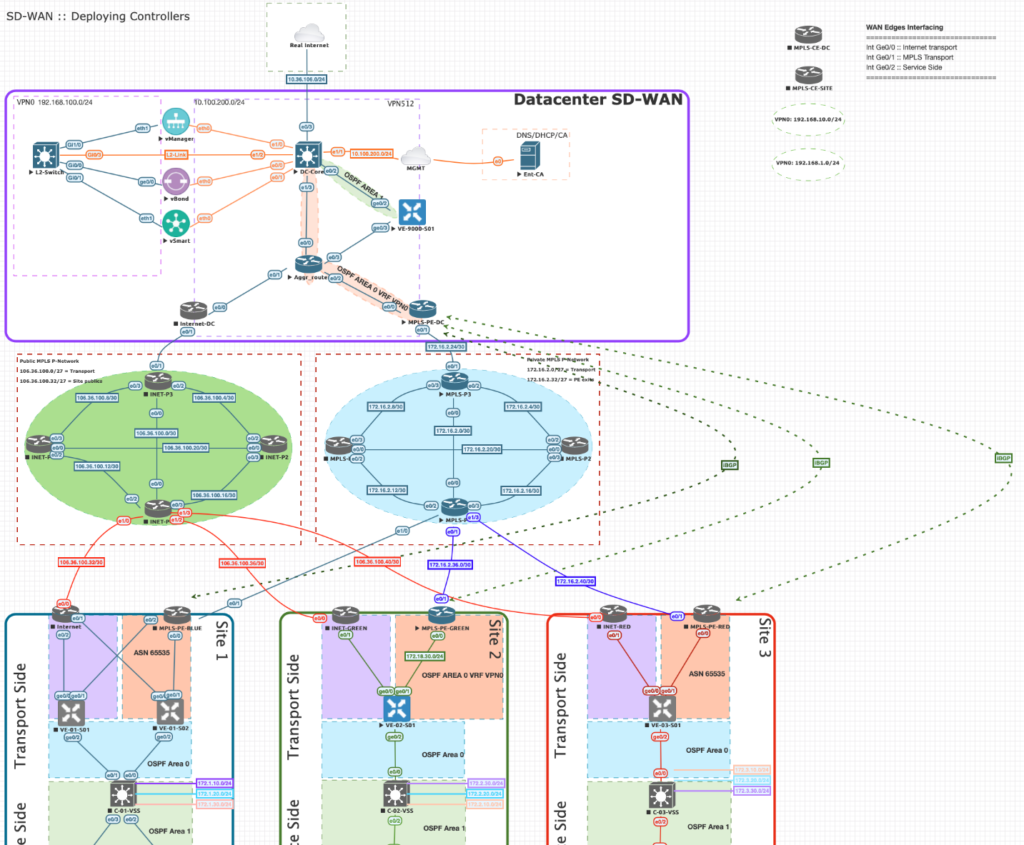
Before we jump in adding vEdges to controllers it’s good to know how many roads lead to Rome. The Cisco SD-WAN solution has two types of software platforms:
- vEdge (Viptela OS)
- IOS-XE SD-WAN (IOS-XE with SD-WAN)
Both software platforms run within both physical and virtual appliances.
Also there are three ways of onboarding:
- Automated Deployment (PnP and ZTP)
- Bootstrap
- Manual
I’m not going into details how we provision all WAN Edges as I’m then replicating the initial source of information. As most of the engineers try to get some hands-on experience by labbing in EVE-NG I will start with the vEdge Cloud WAN Edge.
For detailed information about all WAN Edges and onboarding principle please check the Cisco Validated Design zone. Please refer to the resources section below.
The vEdge Cloud support either ZTP Provisioning or manual. Since I use a separate Enterprise CA I’ve chosen the latter.
:: Prerequisites
In this stage I assume you have setup your lab, added controllers, done some cool stuff with root certificates and signing these in order to setup DTLS tunnels between the controllers.
vmanage# show control connections
PEER PEER PEER
PEER PEER PEER CONFIGURED SITE DOMAIN PEER PRIV PEER PUB
INDEX TYPE PROT SYSTEM IP SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION REMOTE COLOR STATE UPTIME
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 vsmart dtls 1.1.1.3 1.1.1.3 9000 1 192.168.100.251 12346 192.168.100.251 12346 testlab.local default up 0:00:17:10
0 vbond dtls 1.1.1.2 1.1.1.2 0 0 192.168.100.252 12346 192.168.100.252 12346 testlab.local default up 0:00:16:54
1 vbond dtls 0.0.0.0 - 0 0 192.168.100.252 12346 192.168.100.252 12346 testlab.local default up 0:00:16:54
2 vbond dtls 0.0.0.0 - 0 0 192.168.100.252 12346 192.168.100.252 12346 testlab.local default up 0:00:17:09
3 vbond dtls 0.0.0.0 - 0 0 192.168.100.252 12346 192.168.100.252 12346 testlab.local default up 0:00:17:09 vsmart# show control connections
PEER PEER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB
INDEX TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT REMOTE COLOR STATE UPTIME
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 vbond dtls 0.0.0.0 0 0 192.168.100.252 12346 192.168.100.252 12346 default up 0:00:21:12
0 vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12346 192.168.100.250 12346 default up 0:00:16:17
1 vbond dtls 0.0.0.0 0 0 192.168.100.252 12346 192.168.100.252 12346 default up 0:00:21:13 vbond# show orchestrator connections
PEER PEER
PEER PEER PEER SITE DOMAIN PEER PRIVATE PEER PUBLIC ORGANIZATION
INSTANCE TYPE PROTOCOL SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT REMOTE COLOR STATE NAME UPTIME
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 vsmart dtls 1.1.1.3 9000 1 192.168.100.251 12346 192.168.100.251 12346 default up testlab.local 0:00:21:33
0 vsmart dtls 1.1.1.3 9000 1 192.168.100.251 12446 192.168.100.251 12446 default up testlab.local 0:00:21:33
0 vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12346 192.168.100.250 12346 default up testlab.local 0:00:16:38
0 vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12446 192.168.100.250 12446 default up testlab.local 0:00:16:38
0 vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12546 192.168.100.250 12546 default up testlab.local 0:00:16:37
0 vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12646 192.168.100.250 12646 default up testlab.local 0:00:16:37
Also let’s highlight some settings that are important before we start:
vManage: Administration / Settings
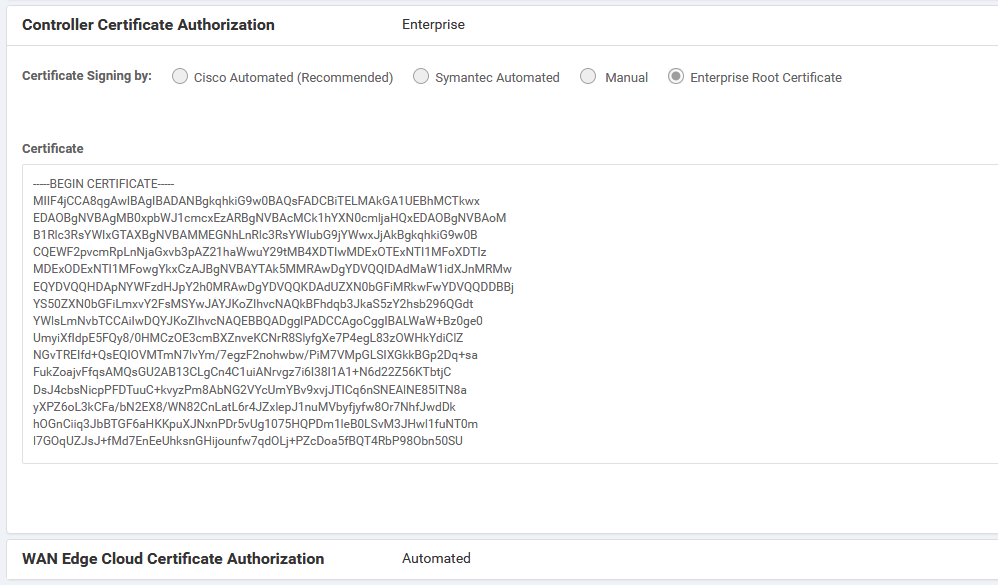
Controller Certificate Authorization was set to Enterprise CA. All controllers have the root-cert installed from this Enterprise CA and all device certificates are signed by that CA.
Note: you don’t have to use a separate CA. You can also use the vManage as a CA via the vshell function.
Some commands to check certificate installation:
- Show certificate root-ca-cert
- Show certificate installed
- Show certificate validity
:: Prepare vEdge
Preparing a vEdge means two things:
- Prepare bootstrap config or skinny configuration
- Get IP reachability
The latter is needed to onboard the device into the fabric. The first one makes sure it gets that IP reachability. The MPLS-PE nodes are already setup with iBGP and MPLS, so pointing with a default route to the PE nodes would be sufficient. Also make sure the Local Tail ip range (/30) is know in your datacenter.
Important to note that we choose for Automatic WAN Edge Cloud Authorization. The vManage will generate and sign the certificate for you.
To summarize:
The Enterprise CA acts as a CA for all controllers and contains your own properties
The vManage (can) act as the CA for all WAN Edges and is generated as a Viptela certificates which is signed by the vManage. The vManage has the root-cert for both Viptela and your own CA.
Since I’m labbing a lot for SD-WAN there is an old configuration on VE-02-S01.
Let’s erase it first:
VE-02-S01 login: admin
Password:
Welcome to Viptela CLI
admin connected from 127.0.0.1 using console on VE-02-S01
VE-02-S01#
VE-02-S01#
VE-02-S01# request reset ?
Possible completions:
configuration Reset to default configuration
logs Clear logs
VE-02-S01# request reset configuration ?
Possible completions:
| <cr>
VE-02-S01# request reset configuration
Are you sure you want to reset to default configuration? [yes,NO] yes
VE-02-S01# Sat Sep 26 13:25:03 CEST 2020: The system is going down for reboot NOW!
Stopping services...
acpid: exiting
ok: down: acpid: 0s, normally up
ok: down: button: 3990s, normally up
ok: down: cloudinit: 3939s, normally up
ok: down: ephemeral: 0s, normally up
ok: down: getty-tty1: 0s, normally up
<omitted>After reboot the vEdge will return with a default config shown below:
system
host-name vedge
admin-tech-on-failure
no route-consistency-check
vbond ztp.viptela.com
aaa
auth-order local radius tacacs
usergroup basic
task system read write
task interface read write
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup tenantadmin
!
user admin
password $6$TK6lEx1f/KWa/kX4$nezPbtMPFcE0wUTQMauGN/RzwWdPPkOeKh5JsxxqVE.0psruUPrWV7q0t/omuwuoRhJia
!
!
logging
disk
enable
!
!
!
omp
no shutdown
graceful-restart
advertise connected
advertise static
!
security
ipsec
authentication-type ah-sha1-hmac sha1-hmac
!
!
vpn 0
interface ge0/0
ip dhcp-client
ipv6 dhcp-client
tunnel-interface
encapsulation ipsec
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
!
no shutdown
!
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
!Before we start we need to gather some mandatory information to configure the vEdge:
- Sited-id: 2
- System-IP: 6.1.1.1
- Org: testlab.local
- vBond IP: 192.168.100.252
- Local tail between VE-02-S01 and MPLS-PE-GREEN: 172.18.30.0/24
- Default route to 172.18.30.2
The skinny configuration:
!
system
host-name VE-02-S01
system-ip 6.1.1.1
site-id 2
admin-tech-on-failure
no route-consistency-check
organization-name testlab.local
clock timezone Europe/Amsterdam
vbond 192.168.100.252
!
vpn 0
!
no interface ge0/0
interface ge0/1
ip address 172.18.30.2/24
no shutdown
tunnel-interface
encapsulation ipsec
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
allow-service sshd
allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
!
no shutdown
!
ip route 0.0.0.0/0 172.18.30.1
!
vpn 512
interface eth0
ip dhcp-client
ipv6 dhcp-client
no shutdown
!
commit and-exit
!Make sure you do some basic check for connectivity. We ping the next-hop address and the vBond’s IP address:
Ping local tail;
VE-02-S01# ping vpn 0 172.18.30.2
Ping in VPN 0
PING 172.18.30.2 (172.18.30.2) 56(84) bytes of data.
64 bytes from 172.18.30.2: icmp_seq=1 ttl=64 time=0.171 ms
64 bytes from 172.18.30.2: icmp_seq=2 ttl=64 time=0.066 ms
64 bytes from 172.18.30.2: icmp_seq=3 ttl=64 time=0.014 ms
64 bytes from 172.18.30.2: icmp_seq=4 ttl=64 time=0.030 ms
64 bytes from 172.18.30.2: icmp_seq=5 ttl=64 time=0.030 ms
<omitted>
VE-02-S01# ping vpn 0 192.168.100.252
Ping in VPN 0
PING 192.168.100.252 (192.168.100.252) 56(84) bytes of data.
64 bytes from 192.168.100.252: icmp_seq=1 ttl=58 time=40.0 ms
64 bytes from 192.168.100.252: icmp_seq=2 ttl=58 time=41.0 ms
<omitted>
:: Getting the DTLS tunnels up
Checking some things before we continue:
VE-02-S01# show certificate root-ca-cert | i Viptela
Subject: O=Cisco, OU=Albireo, CN=Viptela SubCA
VE-02-S01#
VE-02-S01#
VE-02-S01# show certificate installed
VE-02-S01#Check status main dashboard on vManage:
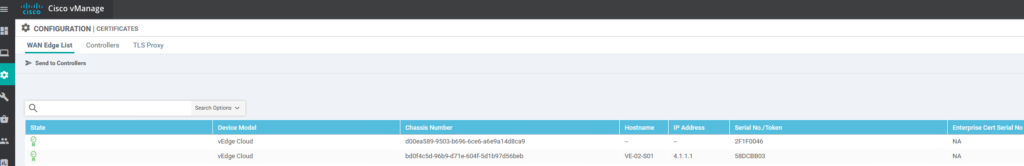
Go to Configuration / Certificates:
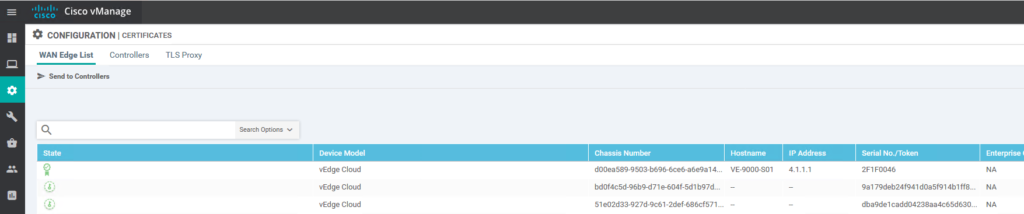
As you can see we already uploaded the Viptela serial file and this has been send to the vBond to enable authentication:
You can check via the following command piped with the chassis number I’m going to use:
vbond# show orchestrator valid-vedges | i bd0f
orchestrator valid-vedges bd0f4c5d-96b9-d71e-604f-5d1b97d56bebAfter uploading the Viptela file you can choose to send the information to vBond. With the above command you can check if vBond has the information to authorize a new vEdge. Otherwise the process will fail.
:: Onboard vEdge
We are going to perform the following tasks:
- Upload root-cert-chain:
- Request activation with chassis-number and One Time Password from vManage / Configuration / Certificates
- Check status and control tunnels
Upload root certificate chain to vEdge:
Logon to CA Server:
Last login: Sat Sep 26 05:12:30 2020 from 10.100.200.50
root@ubuntu1804-pfne:~#
root@ubuntu1804-pfne:~#
root@ubuntu1804-pfne:~#
root@ubuntu1804-pfne:~# ls -lha
total 60K
drwx------ 5 root root 4.0K Sep 19 14:11 .
drwxr-xr-x 23 root root 4.0K Jun 10 2018 ..
-rw------- 1 root root 5.5K Sep 26 05:26 .bash_history
-rw-r--r-- 1 root root 3.1K Apr 9 2018 .bashrc
drw------- 7 root root 4.0K Sep 19 13:51 ca
drwx------ 3 root root 4.0K Jan 19 2020 .cache
drwx------ 3 root root 4.0K Jan 19 2020 .gnupg
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 12 Jun 10 2018 .python_history
-rw------- 1 root root 1.0K Sep 19 14:10 .rnd
-rw------- 1 root root 13K Sep 19 14:11 .viminfo
root@ubuntu1804-pfne:~# cd ca
root@ubuntu1804-pfne:~/ca# ls -lha
total 64K
drw------- 7 root root 4.0K Sep 19 13:51 .
drwx------ 5 root root 4.0K Sep 19 14:11 ..
-rw------- 1 root root 2.1K Jan 19 2020 cacert.pem
drw------- 2 root root 4.0K Jan 19 2020 certs
drw------- 2 root root 4.0K Jan 19 2020 crl
-rw-r--r-- 1 root root 3.2K Sep 19 13:51 index.txt
-rw-r--r-- 1 root root 21 Sep 19 13:51 index.txt.attr
-rw-r--r-- 1 root root 21 Sep 15 12:53 index.txt.attr.old
-rw-r--r-- 1 root root 3.1K Sep 15 12:53 index.txt.old
drw------- 2 root root 4.0K Sep 19 13:51 newcerts
drw------- 2 root root 4.0K Jan 19 2020 private
drw------- 2 root root 4.0K Sep 19 14:11 request
-rw-r--r-- 1 root root 5 Sep 19 13:51 serial
-rw-r--r-- 1 root root 5 Sep 15 12:53 serial.old
-rw-r--r-- 1 root root 1.2K Jun 12 13:08 vedge1.csr
-rw-r--r-- 1 root root 0 Jun 12 13:09 vedge1.pem
-rw-r--r-- 1 root root 1.2K Jun 12 13:08 vedge2.csr
root@ubuntu1804-pfne:~/ca# cat cacert.pem
-----BEGIN CERTIFICATE-----
MIIF4jCCA8qgAwIBAgIBADANBgkqhkiG9w0BAQsFADCBiTELMAkGA1UEBhMCTkwx
EDAOBgNVBAgMB0xpbWJ1cmcxEzARBgNVBAcMCk1hYXN0cmljaHQxEDAOBgNVBAoM
B1Rlc3RsYWIxGTAXBgNVBAMMEGNhLnRlc3RsYWIubG9jYWwxJjAkBgkqhkiG9w0B
CQEWF2pvcmRpLnNjaGxvb3pAZ21haWwuY29tMB4XDTIwMDExOTExNTI1MFoXDTIz
MDExODExNTI1MFowgYkxCzAJBgNVBAYTAk5MMRAwDgYDVQQIDAdMaW1idXJnMRMw
EQYDVQQHDApNYWFzdHJpY2h0MRAwDgYDVQQKDAdUZXN0bGFiMRkwFwYDVQQDDBBj
YS50ZXN0bGFiLmxvY2FsMSYwJAYJKoZIhvcNAQkBFhdqb3JkaS5zY2hsb296QGdt
YWlsLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBALWaW+Bz0ge0
UmyiXfIdpE5FQy8/0HMCzOE3cmBXZnveKCNrR8SlyfgXe7P4egL83zOWHkYdiClZ
NGvTREIfd+QsEQIOVMTmN7lvYm/7egzF2nohwbw/PiM7VMpGLSIXGkkBGp2Dq+sa
FukZoajvFfqsAMQsGU2AB13CLgCn4C1uiANrvgz7i6I38I1A1+N6d22Z56KTbtjC
DsJ4cbsNicpPFDTuuC+kvyzPm8AbNG2VYcUmYBv9xvjJTICq6nSNEAlNE85lTN8a
yXPZ6oL3kCFa/bN2EX8/WN82CnLatL6r4JZxlepJ1nuMVbyfjyfw8Or7NhfJwdDk
hOGnCiiq3JbBTGF6aHKKpuXJNxnPDr5vUg1075HQPDm1leB0LSvM3JHwl1fuNT0m
l7GOqUZJsJ+fMd7EnEeUhksnGHijounfw7qdOLj+PZcDoa5fBQT4RbP98Obn50SU
XKEfhVzOxAy/KmePHwV5kUuYAjmF6ErqfthxnlvCYFglb+J6Z9j6DXI2mnSsiw9L
/5rdN/FKigvV6qL4pF/PNA9Opm7HdvO41yN48TMjiIHPYNYCVQkDxrXr6bXA1diD
SM2IRqzVtDqAIFgJq4WB1LxA8MFCl6Q6lNVpagO15EVWwrG4va7VgOdhEjgmxIzd
VRvS4+o3mxWTHTwH16VaymWaqCV9RNqnAgMBAAGjUzBRMB0GA1UdDgQWBBTImkv6
ExunbxMxxVeSIOrQGJ/AMzAfBgNVHSMEGDAWgBTImkv6ExunbxMxxVeSIOrQGJ/A
MzAPBgNVHRMBAf8EBTADAQH/MA0GCSqGSIb3DQEBCwUAA4ICAQCPwngBMrCgyLRR
In5k3o3/RvEmtQscYcMZLfkr6J5n28m+p21r9NKGHRG/dgz/qPACk5aG6jQgMP8w
am3cgKoufGXQghynIX1xSuwrSjhiQ0hP3BKm7bac+7P0rbYL51Z02yEvphOjUzjX
/pBINUIgkki9t+6SAaeUyPHpLCKQ4VthErh/ewY1d4zezKuyRuNDDdh26UyifrQ0
3hzASr5dFdxnvLxIop9apDwNksqMZnhEuVm8NynbTAE182w7vHMZ0udH5k/ierB+
VWLvSXP5+796L1OW+bf38lcl5rbSnjkmFXikQrr+iBzfzfiliKmjjxmbat0tA0Sd
Wfpo2sy4YZXLIZMjY3KwJlvw7ha305GfmFxAo8a91GdhUbvKHjCvLtbEAYkKlOcX
zAGod63LnvTQKb0rFvUrZBsFLPZAvG5XRK9ixPeyl8Xqf8NmC0Cg9/pCZmhx0e8W
rh26Z3gP1LHNps0lVN45cR8xNnNsTlx3yOanoF/ZhhovdWADLh2iadODLoGNcS8P
Ewbf0RKtrLhXn8jqeXhvUmRH77jybi0I9CiIlKh2KODHe7FWeWqHeRqx58vdkR/w
Q31NSzwpMpJCtDecIe7TiGkYqy9q89O/mGsxPvQ/d8Cwp/NPzyjYk1qei1mowFd4
+8R/IAgnYtm6RTqal0FRFJS3pwEOfw==
-----END CERTIFICATE-----
root@ubuntu1804-pfne:~/ca#Copy paste the root cert from BEGIN CERTIFICATE to END CERTIFICATE
Login to vEdge:
viptela 19.2.099
VE-02-S01 login: admin
Password:
Welcome to Viptela CLI
admin connected from 127.0.0.1 using console on VE-02-S01
VE-02-S01#
VE-02-S01#
VE-02-S01# vshell
VE-02-S01:~$ vi rootcert.pemIn Vi first enter the “i’ to edit and paste the cert into the screen. After pasting push ESC key and enter “:wq” to save and quit Vi
VE-02-S01:~$ exit
exit
VE-02-S01# request root-cert-chain install /home/admin/rootcert.pem
Uploading root-ca-cert-chain via VPN 0
Copying ... /home/admin/rootcert.pem via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chain
VE-02-S01# Now request to activate vEdge with your chassis-number and OTP (just choose one form the list to claim):
VE-02-S01# request vedge-cloud activate
Value for 'chassis-number' (<Chassis number/uuid of the device>): bd0f4c5d-96b9-d71e-604f-5d1b97d56beb
Value for 'token' (<Serial number of the device>): 9a179deb24f941d0a5f914b1ff8b8483
VE-02-S01#
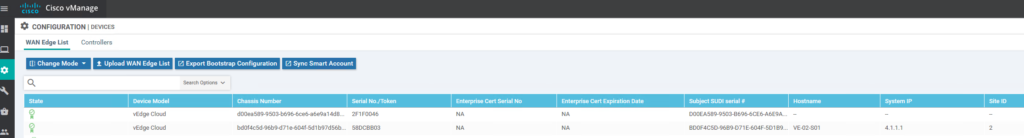
Wait for some time or check vManage / Configuration / Device or Configuration / Certificate. The System-IP and hostname should popup in the list.Check if the tunnels to the controllers are UP and running:
VE-02-S01# show control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT LOCAL COLOR PROXY STATE UPTIME ID
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.1.3 9000 1 192.168.100.251 12446 192.168.100.251 12446 mpls No up 0:00:00:05 0
vbond dtls 0.0.0.0 0 0 192.168.100.252 12346 192.168.100.252 12346 mpls - up 0:00:00:06 0
vmanage dtls 1.1.1.1 9000 0 192.168.100.250 12446 192.168.100.250 12446 mpls No up 0:00:00:06 0
Check for certificate status’:
VE-02-S01# show certificate installed
Installed device certificates
-----------------------------
Certificate:
Data:
Version: 1 (0x0)
Serial Number: 1490860803 (0x58dcbb03)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, CN=5507a138-09ab-4b0f-b44f-6d536b92c428, O=Viptela
Validity
Not Before: Sep 26 12:15:41 2020 GMT
Not After : Sep 24 12:15:41 2030 GMT
Subject: C=US, ST=California, L=San Jose, OU=testlab.local, O=Viptela LLC, CN=vedge-bd0f4c5d-96b9-d71e-604f-5d1b97d56beb-0.viptela.com/emailAddress=support@viptela.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c7:da:51:f7:77:c7:0a:28:56:f7:92:4a:87:79:
bb:8c:a6:66:58:ef:a7:9e:9c:d6:d8:4b:65:6d:c4:
ca:d2:8f:b3:99:6b:6a:f7:08:64:0a:b2:13:ea:03:
b2:a8:01:3f:3d:69:d7:a6:bd:7f:1b:e9:e1:38:ff:
01:12:d2:28:e9:9f:34:67:ac:f4:a0:54:57:fc:b8:
7a:1a:1f:16:d7:59:01:fe:bb:93:64:b2:a2:12:b2:
9c:f2:6a:30:8a:f6:84:44:b4:0a:ba:29:a0:a3:d3:
14:d5:eb:5b:c6:f8:a6:c2:41:85:7d:fa:6c:9b:62:
a4:91:3d:ca:9c:fa:4d:1d:34:4e:ad:41:9f:d2:8d:
6c:0d:3d:cf:41:d7:95:a8:e1:21:f6:01:ec:be:c7:
8f:dc:56:0d:e0:72:90:5c:58:f2:86:0f:b6:3d:74:
c5:f6:a6:2c:4e:74:09:c4:fa:79:35:36:ef:36:bc:
15:4a:dd:70:eb:80:db:1a:17:66:07:11:8d:aa:ab:
c4:1b:ef:3e:96:aa:48:06:dc:da:04:cd:08:cf:ae:
26:d7:9a:7f:73:43:75:24:59:b1:80:85:03:f5:ea:
3a:74:77:4c:e1:6d:8f:c8:24:5d:01:29:c9:c4:8c:
9c:3c:b7:9c:a7:e3:33:37:13:5b:08:a1:1b:c2:2d:
50:e9
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
71:ab:49:e6:20:07:92:d3:33:cc:02:01:31:91:f7:cf:46:35:
83:cf:93:49:50:b5:74:92:89:da:d2:6a:e3:12:6d:95:04:f6:
11:be:58:e6:6e:a5:17:fd:60:c4:f7:e1:51:7b:31:38:6c:76:
03:2b:2a:71:3f:0b:71:6e:eb:59:4d:20:d3:98:44:a1:1e:c2:
02:55:49:19:83:3a:1d:6f:83:12:7f:8b:fc:2c:ac:6b:fd:95:
a7:02:0b:b6:f8:f4:77:23:40:20:4e:81:4d:fe:45:6a:e9:5f:
82:ef:10:20:4c:f1:f1:ce:4a:93:6a:a4:3c:5a:04:f1:72:5d:
1c:8e:21:53:3d:6c:58:86:0a:fa:0b:19:ce:45:cb:cc:d5:8e:
fb:b5:b1:6a:1e:3c:bb:1d:cc:6f:e4:be:93:0d:79:b2:b8:e1:
04:c6:54:f8:5e:51:36:52:b1:df:b5:57:d5:be:64:9c:0d:04:
b3:8c:8b:00:92:2a:42:a4:8b:b7:a5:f8:bd:e4:64:9c:c4:59:
4d:12:37:78:10:27:50:84:03:a8:6d:51:95:8f:4a:0a:fe:b5:
c2:e4:d3:7c:c6:0c:30:bd:fd:7e:d5:29:dc:02:c7:55:bb:d1:
c8:09:80:e7:1c:4b:c9:50:48:ad:a2:e1:14:2e:5d:9e:bc:3f:
4c:3e:8b:1e
VE-02-S01# show certificate root-ca-cert | i Viptela
Subject: O=Cisco, OU=Albireo, CN=Viptela SubCA
Issuer: C=US, CN=5507a138-09ab-4b0f-b44f-6d536b92c428, O=Viptela
Subject: C=US, CN=5507a138-09ab-4b0f-b44f-6d536b92c428, O=Viptela
VE-02-S01# show certificate root-ca-cert | i testlab
Issuer: C=NL, ST=Limburg, L=Maastricht, O=Testlab, CN=ca.testlab.local/emailAddress=jordi.schlooz@gmail.com
Subject: C=NL, ST=Limburg, L=Maastricht, O=Testlab, CN=ca.testlab.local/emailAddress=jordi.schlooz@gmail.com
VE-02-S01#
VE-02-S01# show certificate validity
The certificate issued by 5507a138-09ab-4b0f-b44f-6d536b92c428 is valid from Sep 26 12:15:41 2020 GMT (Current date is Sat Sep 26 15:41:55 GMT 2020) & valid until Sep 24 12:15:41 2030 GMT
VE-02-S01#
Check vManage:
![Cisco мМападе
% DASHBOARDI мат DASHa0AR0
St.t“ (То“ ' 2)
Ир
Edge • 2
sa. H„hh 2)
Fu]I
[ WAN C—tivify
WAN C—tNRy
« МЬ.рз
мьр, мьр,
100 мьр,. 500 мьр,](https://www.theansweris101010.network/wp-content/uploads/2020/09/image-5-1024x227.png)
Your vEdge is up and running.
:: Conclusion
We have observed that the vEdge has a different certificate installed then the vBond, vSmart and vManage. The root certificate on the controllers from my own CA have a validity of 3 years and each signed device certificate is valid for 1 year basis on O=testlab.local and OU=testlab.local
The vEdge has a O=Viptela LLC based on OU=testlab.local and is valid for 10 years. So this means the vManage has delivered a different device certificate. Before onboarding we saw that the vEdge has a root certificate pre-installed for O=Viptela LLC. The controllers also have a bunch of root-certificate pre-installed. With this match the DTLS tunnels are setup to the controllers.
Also for the observant ones I use 20.3.1 for all my controllers. This vEdge has version 19.2.099 and is not on the compatibility list. Reason for this is that this release is deferred. But it still works fine.
I hope I can onboard the CSR SD-WAN IOS-XE device as well in the next coming days. After this I’m going to learn and test templating. Also I’m thinking of running through the WAN Edge replacement procedure to update the WAN Edge to 20.3.1.
Hope you find it usefull and as always the answer could be 42.
